Confidential computing is a know-how and method that encrypts and shops a company’s most delicate knowledge in a safe portion of a pc’s processor — generally known as the Trusted Execution Surroundings (TEE) — whereas it’s processed and in use.
It’s a fast-growing cloud computing method that has gotten buy-in and assist from a wide range of {hardware}, software program, and cloud distributors. Learn on to be taught extra about confidential computing, the way it works, and the way it advantages enterprise knowledge safety efforts.
How Does Confidential Computing Work?
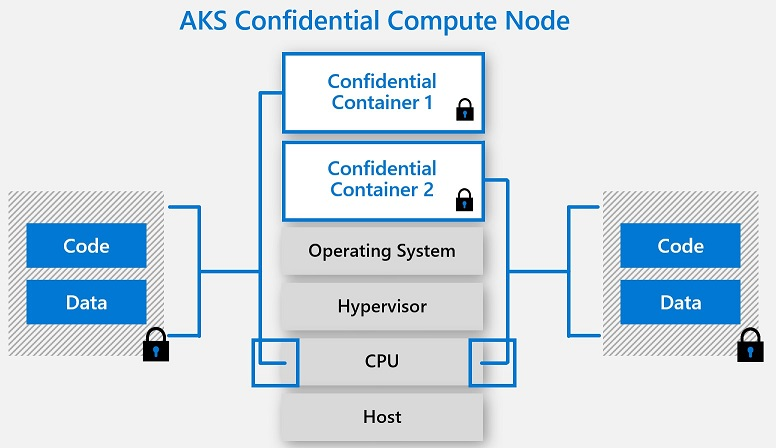
Confidential computing is all about utilizing know-how to create an remoted secure area, in any other case generally known as a Trusted Execution Surroundings (TEE), for probably the most delicate knowledge and knowledge processing directions. Throughout confidential computing, the TEE and a preselected dataset are separated from the remainder of the computing setting, together with the working system, the hypervisor, uninvolved functions, and even cloud service suppliers.
Not like different kinds of knowledge processing, in confidential computing knowledge doesn’t must be decrypted in reminiscence and uncovered to exterior safety vulnerabilities with the intention to be processed. As an alternative, it is just decrypted within the Trusted Execution Surroundings, which depends on hardware-based coprocessor safety, embedded encryption keys, and embedded attestation mechanisms to make sure that solely licensed functions, customers, and programming code can entry the TEE and the information it homes. Knowledge processed inside a Trusted Execution Surroundings is totally invisible to all computing parts that aren’t a part of the designated TEE, and knowledge at all times stays encrypted whereas in transit or saved exterior the TEE.
Additionally learn: Encryption: How It Works, Varieties, and the Quantum Future
7 Advantages of Utilizing Confidential Computing
Confidential computing provides a number of advantages for safer dealing with of delicate knowledge whereas in use.
1. Added safety in shared, untrusted, or unfamiliar environments
The trendy computing panorama, particularly when the cloud’s concerned, means your knowledge is usually saved in environments which can be uncovered to 3rd events, completely different departments, and public customers. There’s restricted native safety constructed into cloud environments, particularly in your most delicate knowledge when it’s in use. Confidential computing strategies and applied sciences give your delicate knowledge extra safeguards, whatever the computing setting.
2. Safe knowledge enter and output
The one time knowledge is decrypted through the confidential computing course of is when the TEE has taken a number of steps to make sure that solely licensed programming code is coming into the setting. In any respect different occasions, delicate knowledge stays encrypted, including extra privateness and safety whereas knowledge is in transit or saved in one other a part of the computing setting.
3. Equal give attention to safety and cloud computing capabilities
Historically, companies have both needed to course of delicate knowledge in reminiscence with main safety dangers or restrict their delicate knowledge processing with the intention to shield it; neither strategy is right for optimum knowledge usability and outcomes. Confidential computing makes it so customers can reap the benefits of the ability and complexity of a cloud computing setting whereas nonetheless defending their delicate knowledge to the utmost diploma.
4. Distant high quality assurance capabilities
Confidential computing structure is designed for distant high quality assurance and safety administration. Distant verification and attestation make it simpler for safety admins to handle a distributed community whereas nonetheless defending and monitoring the Trusted Execution Surroundings.
5. Simpler detection and prevention of unauthorized entry
Constructed-in attestation allows the confidential computing structure to confirm programming codes earlier than they will enter the TEE; confidential computing know-how may also fully shut down the computing course of if an unauthorized set of code makes an attempt to tamper with or acquire entry to the TEE. Such a computing supplies a really perfect mixture of hands-off safety protocols and visibility into unauthorized community visitors.
6. Compatibility with knowledge privateness and compliance necessities
Compliance legal guidelines like GDPR and HIPAA require firms to retailer and use knowledge in particular methods to take care of compliance. It’s not at all times simple to stick to those requirements in a public cloud setting, however with the extra security measures confidential computing supplies for delicate knowledge, companies can extra simply adjust to a wide range of knowledge privateness and safety rules whereas nonetheless taking advantage of their knowledge.
7. Safety for knowledge in use
Though different strategies are rising and getting used as we speak, confidential computing is without doubt one of the few encryption methods that successfully protects knowledge in use. Most different encryption approaches shield knowledge at relaxation and knowledge in transit solely.
Additionally learn: Exfiltration Can Be Stopped With Knowledge-in-Use Encryption
Confidential Computing Use Instances
Confidential computing’s protections make it perfect for quite a lot of delicate knowledge use instances.
Safe third-party outsourcing
Outsourcing sure enterprise capabilities to 3rd events is frequent lately, however it may be a dangerous transfer in case your knowledge isn’t solely safe. The enclaved strategy taken with TEEs makes it so your inside group can shield and primarily disguise delicate knowledge from unauthorized third-party customers, permitting them to focus solely on the components of your computing course of they should entry whereas trusted members of your group handle delicate knowledge processes.
Encryption to mitigate insider threats
As a result of confidential computing means delicate knowledge is encrypted always (till it’s processed within the TEE), even members of your inside group can’t entry and interpret this protected knowledge with out authorization. This characteristic of confidential computing protects in opposition to rogue customers inside the community in addition to customers who fall sufferer to credential phishing assaults.
Protected public cloud use
Companies are transferring a lot of their workflows and operations to the cloud, however a few of the largest enterprises are nonetheless hesitant to maneuver their most delicate workloads to a public cloud setting. With confidential computing within the combine, enterprises can really feel extra assured and keep extra management over their delicate knowledge at relaxation, in transit, and in use, even in a public cloud setting with third-party distributors and customers that observe various safety protocols.
See the Finest Third-Get together Danger Administration Software program & Instruments
IoT knowledge processing
Web of Issues (IoT) gadgets generate large quantities of information which can be hardly ever saved in a safe style. Confidential computing is more and more getting used to create enclaves the place IoT knowledge may be processed in a confidential manner that ensures the information isn’t tampered with.
Collaborative knowledge analytics and knowledge utilization
Analyzing broader patterns throughout a company or a whole business usually requires customers to entry delicate knowledge exterior of their regular scope of labor. Providing an alternate and safer strategy, confidential computing helps safe and collaborative knowledge analytics, permitting customers to handle and consider their very own inputs and acquire insights right into a sprawling dataset with out seeing different customers’ inputs or outputs. This strategy to analytics is particularly useful in industries like insurance coverage and healthcare the place analyzing and deciphering broad patterns can inform insurance coverage charges and diagnostics, respectively.
Blockchain and crypto safety
The encryption concerned in confidential computing is particularly helpful in a blockchain setting. Frequent confidential computing use instances embrace good contract, non-public key, and cryptographic operations administration.
Machine studying coaching
For organizations that wish to work with or prepare a machine studying mannequin with out exposing their coaching dataset, confidential computing is a viable answer for privateness. The machine studying mannequin may be positioned in a TEE enclave, permitting knowledge house owners and customers to share their knowledge with the mannequin and prepare it in an invisible, remoted setting.
Confidential Computing Consortium (CCC)
The Confidential Computing Consortium (CCC) is a Linux Basis venture neighborhood that’s made up of varied tech leaders. The CCC works to advance confidential computing capabilities and adoption by means of collaboration on high-profile and open-source confidential computing tasks. Its present tasks embrace Enarx, Gramine, Keystone, Occlum, Open Enclave SDK, Veracruz, and Veraison.
The group is led by two governing officers, a board of administrators, committee chairs, and varied workers. Members of the Confidential Computing Consortium embrace Intel, Meta, Microsoft, Google, Accenture, Huawei, Crimson Hat, Accenture, Anjuna, AMD, Canonical, Cisco, Fortanix, Nvidia, Ruby, and VMware.
Confidential Computing vs. Homomorphic & Knowledge-in-Use Encryption
Confidential computing, totally homomorphic encryption (FHE), and data-in-use encryption share many similarities, particularly since all of them give attention to securing knowledge in use, however every creates a barely completely different encryption and utilization state of affairs.
Knowledge-in-use encryption could possibly be checked out as one element of confidential computing; it’s used to maintain knowledge encrypted till it’s in an remoted TEE, the place it might then be decrypted by licensed keys and code. Confidential computing additionally takes this strategy to encryption and remoted knowledge processing, nevertheless it’s a much wider idea that features different applied sciences and techniques, like different kinds of encryption, safe execution environments and storage, safe communication protocols, and safe key administration options.
Absolutely homomorphic encryption is an previous concept that has solely just lately superior sufficient to appreciate its promise. This strategy to knowledge safety encrypts knowledge all through its whole lifecycle, even when it’s being utilized in computations. Knowledge inputs are encrypted throughout processing and computing, and outcomes come out encrypted as effectively. In distinction, each confidential computing and data-in-use encryption enable knowledge to be decrypted and seen when it’s within the Trusted Execution Surroundings.
In concept, FHE has some main safety advantages since knowledge is encrypted all through the computing course of. Nevertheless, this kind of encryption requires massive quantities of overhead, is complicated to handle, and has potential for customers to make modifications to encrypted knowledge with out different customers ever realizing, thus damaging knowledge integrity. FHE remains to be early in its improvement and will overcome a few of these shortcomings over time.
Additionally learn: Homomorphic Encryption Makes Actual-World Positive factors, Pushed by Google, IBM, Microsoft
Prime 3 Confidential Computing Firms
Confidential computing is a fancy course of that requires superior software program, {hardware}, and cloud computing applied sciences. As such, there are numerous confidential computing firms and leaders that concentrate on completely different components of the confidential computing structure. We’ve taken a better take a look at three of those leaders under. Different main confidential computing firms embrace IBM, Google (Alphabet), AWS, and Fortanix, and promising startups like Anjuna Safety, Opaque Techniques, Inpher, Gradient Movement, HUB Safety, Edgeless Techniques, Profian, Secretarium, and Decentriq.

Intel
Intel is without doubt one of the initially gamers within the confidential computing area. Intel Software program Guard Extensions (SGX) is probably the most generally used hardware-based enclave answer for confidential computing. The corporate additionally manages Undertaking Amber, a zero-trust confidential computing venture, and Intel Belief Area Extensions (TDX), a VM-focused strategy for added privateness and management. Ron Perez, an Intel fellow and chief safety architect at Intel, is the Confidential Computing Consortium’s governing board vice-chair.

Fortanix
Fortanix is taken into account one of many earliest pioneers in confidential computing. Fortanix’s Confidential Computing Supervisor (CCM) is a SaaS answer that helps customers handle TEEs and shield knowledge in use throughout varied cloud environments. Fortanix can be a founding member of the Confidential Computing Consortium.
Microsoft
Microsoft provides a spread of confidential computing options primarily by means of the Azure cloud setting. The Azure confidential computing initiative consists of varied services, akin to confidential VMs and confidential VMs with software enclaves, confidential containers, trusted launch, a confidential ledger, SQL Azure All the time Encrypted, Microsoft Azure Attestation, and Azure Key Vault M-HSM. Stephen Walli, a principal program supervisor for Microsoft Azure, is the governing board chair for the Confidential Computing Consortium.
See the Prime Enterprise Encryption Merchandise
Backside Line: Confidential Computing
The trendy enterprise community isn’t simply an on-premises setting or easy knowledge middle. It consists of third-party companions and functions, public and hybrid clouds, and different exterior components that really feel considerably past the management of conventional community safety options. Processing knowledge in these environments is extra perilous than ever. For firms that wish to enhance their safety and management on the knowledge stage, no matter what their community seems to be like or who’s utilizing it, confidential computing provides an answer to take care of knowledge safety whereas upholding knowledge integrity and enabling high-performance knowledge duties.
Learn subsequent: Safety Issues for Knowledge Lakes






