Blockchain know-how is predicted to recover from $1 trillion by 2032, in keeping with a market analysis prognosis, specializing in blockchain for explicit enterprise segments.
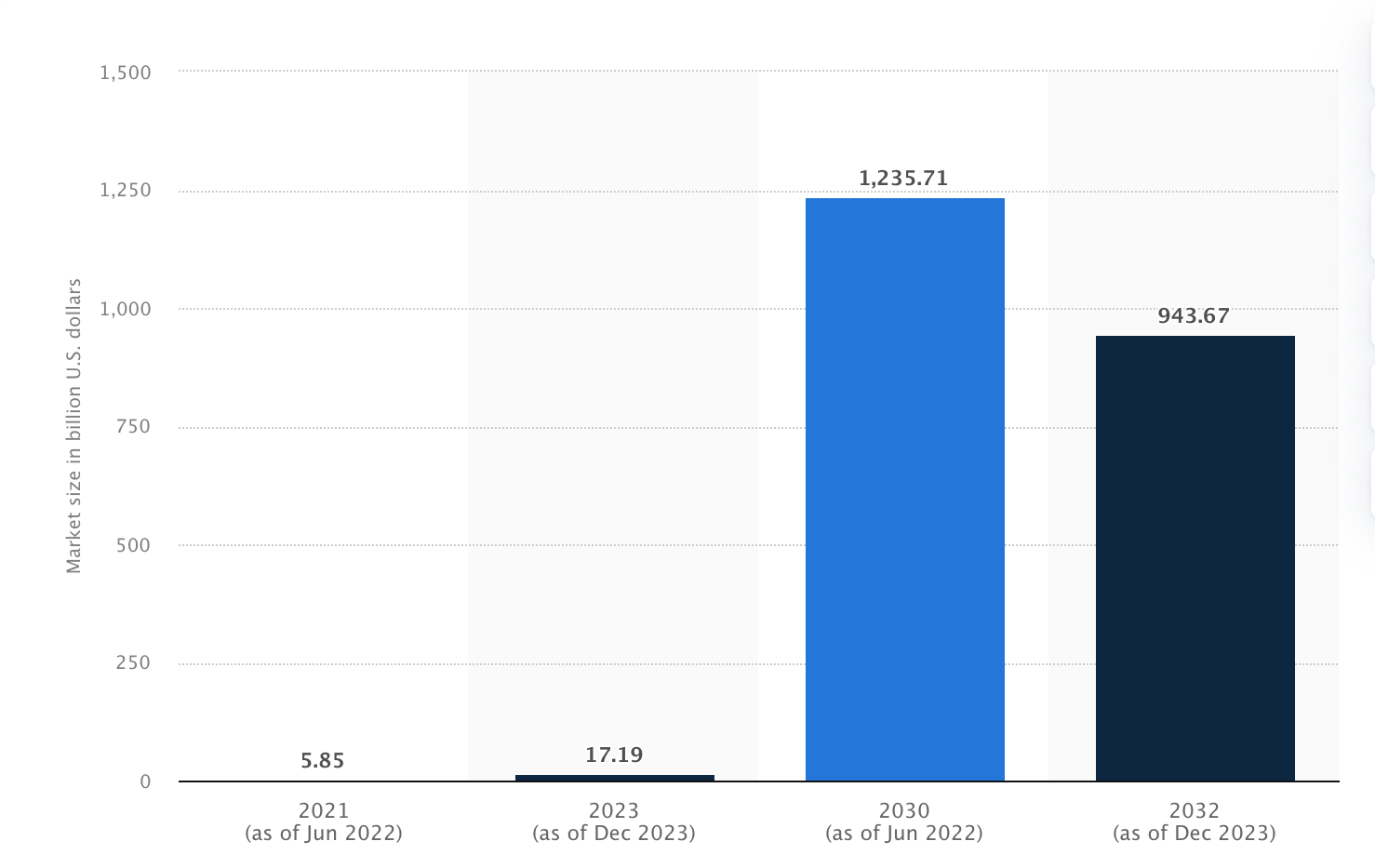
Blockchain know-how cloud market measurement, with a prognosis for 2030, Statista
That is considerably awaited as a result of blockchain developer groups have discovered a large use selection for decentralization—in gaming, actual property, logistics, medical care, and finance.
One of many explanations for this upsurge is that know-how is usually characterised as being extraordinarily safe. However what stands behind it?
One of many central parts including to blockchain safeness is a hash that meets the encrypted necessities wanted to guard info.
What Is a Hash? Definition, Rationalization, and Position in Blockchain
Blockchain hashing is a course of that takes any sort of knowledge—a file or transaction—and turns it right into a fixed-length wire of particular symbols.

The ensuing wire is named the hash worth, a novel illustration of the enter knowledge no matter its measurement. It doesn’t matter in case you hash a small textual content or a extremely detailed transaction file; the output of hashing will at all times be of the identical size.
The hash worth is usually known as a “digital fingerprint.” The character of this fingerprint is such that, with just one modified little bit of the unique knowledge, it’ll produce a totally totally different hash.
The most typical hash operate utilized within the blockchain is SHA-256 or Safe Hash Algorithm-256 bit. It turns into the essential constructing block for anybody who desires to develop a blockchain answer as a result of it supplies wholeness and safeness to knowledge.
Different hash capabilities embody however will not be restricted to MD5 and SHA-3; nevertheless, every has totally different stipulations for safety, and therefore not all of them could be sturdy sufficient to be utilized for blockchain functions.
Some Primary Info About Hashes
One of the vital roles in safe blockchain know-how is performed by hashes, and the rationale they’re so influential is because of numerous their properties:
Fastened-Size Output
Irrespective of how large or small the enter knowledge is, the hashing know-how will at all times generate a results of a set size. As an illustration, SHA-256 produces a 256-bit hash whether or not you’re hashing a single phrase or a complete doc.
Predictable
The selfsame enter will at all times set free the an identical hash. Due to this sameness, blockchain methods can confirm knowledge by hash comparisons. If even a single determine within the enter adjustments, the hash turns into fully totally different.
Collision-Resistant
No two totally different parts of information ought to ever create the identical hash. In different phrases, it signifies that every enter of information has a novel “digital fingerprint,” thereby lowering any risk of collision—a scenario the place two an identical hashes happen.
Non-Reversible
Hashing is a one-way operate as a result of it’s slightly simple to create a hash from knowledge, however not possible to recreate from the hash what the unique knowledge was.
How Blockchain Hashing Fortifies Safety
As we talked about above, blockchain hashing creates a digital fingerprint for any piece of information, which makes it simple to carry knowledge integrity.

Even changing one letter of the information will completely alter the outcome. In such a means, it’s slightly simple to note the try at tampering with the information—it solely needs to be checked if the hash matches.
Hashing additionally creates a stage of belief in a blockchain system, with the whole lot being verifiable by the hash. There is no such thing as a want for a government to analyze each transaction as a result of members can independently confirm that knowledge is right.
Hashing lastly performs an vital position within the so-called Proof of Work, a mechanism used on most blockchains, together with the first-introduced Bitcoin.
The miners in PoW are tasked with fixing a difficult puzzle by discovering a hash that meets sure standards.
The computing energy exerted in fixing such issues is big, and because of this, tampering with a blockchain turns into very tough since all that work must be redone for every block by any person who so needs.
How Hash Know-how Works in a Blockchain: Actual-World Instance
Suppose a person sends 2 Bitcoins to somebody. The transaction particulars, equivalent to sender and receiver, together with the quantity transferred, are added to a block of many different transactions.
This block additionally incorporates some further particulars, equivalent to a file of the time and a ref to the foregoing block.
Subsequent, the whole block is run by a hash operate (like SHA-256), which creates a novel hash worth.
The way it works: blocks hyperlink in such a means that every block has its hash and the hash of the earlier block. That’s, Block 1 has its personal hash, and Block 2 incorporates its hash and a reference to Block 1’s hash.
Block 3 incorporates its hash and Block 2’s hash, and so forth. It kinds a series of blocks in a secured method—therefore the title “blockchain”.
Now, if somebody tries to vary the information in Block 1 (for instance, altering the quantity in a transaction), the hash for Block 1 will change. Since Block 2 leans on Block 1’s hash, it’ll now not match, which breaks the chain.
To cover the intervention, the attacker would then have to rehash Block 1 and each block thereafter, which is a ridiculously excessive computation situation.
Limitations and Counterarguments of Blockchain Hashing
Whereas highly effective, hashing doesn’t come with out its issues. First off, these may be collision assaults, that means that two totally different knowledge produce the identical hash although this might occur very not often with fashionable hash capabilities equivalent to SHA-256.

Theoretically, it’s nonetheless a threat. Consultants in cryptography maintain working exhausting to make even safer hash capabilities, to keep away from collisions.
Quantum computing sooner or later will probably be extra of a menace. These highly-powered computer systems, as some brightest minds assume, could, at some point, crack present hash algorithms and, thus, make it simpler to reverse hashes or discover collisions.
Due to this, researchers are already engaged on creating quantum-resistant algorithms that will rise up in opposition to new threats.
Proof-of-work methods rely closely on hashing in mining, the place miners attempt to outcompete each other by fixing advanced puzzles with hash technology.
Resulting from this truth, such a course of consumes huge power; consequently, the environmental footprint of blockchains equivalent to Bitcoin is beginning to emerge as a priority.






