
Mass exploitation started over the weekend for yet one more essential vulnerability in broadly used VPN software program offered by Ivanti, as hackers already concentrating on two earlier vulnerabilities diversified, researchers stated Monday.
The brand new vulnerability, tracked as CVE-2024-21893, is what’s referred to as a server-side request forgery. Ivanti disclosed it on January 22, together with a separate vulnerability that up to now has proven no indicators of being exploited. Final Wednesday, 9 days later, Ivanti stated CVE-2024-21893 was beneath energetic exploitation, aggravating an already chaotic few weeks. The entire vulnerabilities have an effect on Ivanti’s Join Safe and Coverage Safe VPN merchandise.
A tarnished fame and battered safety professionals
The brand new vulnerability got here to mild as two different vulnerabilities had been already beneath mass exploitation, largely by a hacking group researchers have stated is backed by the Chinese language authorities. Ivanti supplied mitigation steering for the 2 vulnerabilities on January 11, and launched a correct patch final week. The Cybersecurity and Infrastructure Safety Company, in the meantime, mandated all federal companies beneath its authority disconnect Ivanti VPN merchandise from the Web till they’re rebuilt from scratch and operating the newest software program model.
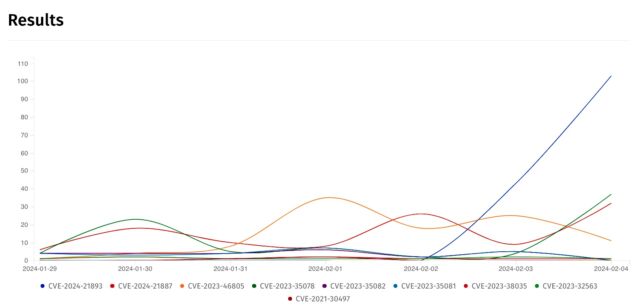
By Sunday, assaults concentrating on CVE-2024-21893 had mushroomed, from hitting what Ivanti stated was a “small variety of clients” to a mass base of customers, analysis from safety group Shadowserver confirmed. The steep line within the right-most a part of the next graph tracks the vulnerability’s meteoric rise beginning on Friday. On the time this Ars publish went dwell, the exploitation quantity of the vulnerability exceeded that of CVE-2023-46805 and CVE-2024-21887, the earlier Ivanti vulnerabilities beneath energetic concentrating on.
Shadowserver
Methods that had been inoculated towards the 2 older vulnerabilities by following Ivanti’s mitigation course of remained large open to the latest vulnerability, a standing that doubtless made it engaging to hackers. There’s one thing else that makes CVE-2024-21893 engaging to risk actors: as a result of it resides in Ivanti’s implementation of the open-source Safety Assertion Markup Language—which handles authentication and authorization between events—individuals who exploit the bug can bypass regular authentication measures and acquire entry on to the executive controls of the underlying server.
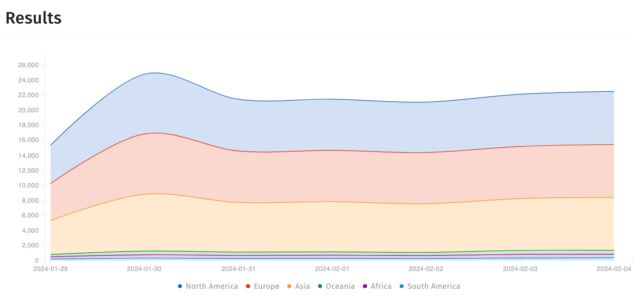
Exploitation doubtless received a lift from proof-of-concept code launched by safety agency Rapid7 on Friday, however the exploit wasn’t the only real contributor. Shadowserver stated it started seeing working exploits a number of hours earlier than the Rapid7 launch. The entire totally different exploits work roughly the identical means. Authentication in Ivanti VPNs happens by the doAuthCheck operate in an HTTP net server binary situated at /root/residence/bin/net. The endpoint /dana-ws/saml20.ws doesn’t require authentication. As this Ars publish was going dwell, Shadowserver counted a little bit greater than 22,000 situations of Join Safe and Coverage Safe.
Shadowserver
VPNs are an excellent goal for hackers in search of entry deep inside a community. The gadgets, which permit staff to log into work portals utilizing an encrypted connection, sit on the very fringe of the community, the place they reply to requests from any machine that is aware of the proper port configuration. As soon as attackers set up a beachhead on a VPN, they’ll typically pivot to extra delicate components of a community.
The three-week spree of continuous exploitation has tarnished Ivanti’s fame for safety and battered safety professionals as they’ve scrambled—typically in useless—to stanch the circulation of compromises. Compounding the issue was a sluggish patch time that missed Ivanti’s personal January 24 deadline by every week. Making issues worse nonetheless: hackers discovered tips on how to bypass the mitigation recommendation Ivanti supplied for the primary pair of vulnerabilities.
Given the false begins and excessive stakes, CISA’s Friday mandate of rebuilding all servers from scratch as soon as they’ve put in the newest patch is prudent. The requirement doesn’t apply to non-government companies, however given the chaos and problem securing the Ivanti VPNs in latest weeks, it’s a commonsense transfer that every one customers ought to have taken by now.

Mass exploitation started over the weekend for yet one more essential vulnerability in broadly used VPN software program offered by Ivanti, as hackers already concentrating on two earlier vulnerabilities diversified, researchers stated Monday.
The brand new vulnerability, tracked as CVE-2024-21893, is what’s referred to as a server-side request forgery. Ivanti disclosed it on January 22, together with a separate vulnerability that up to now has proven no indicators of being exploited. Final Wednesday, 9 days later, Ivanti stated CVE-2024-21893 was beneath energetic exploitation, aggravating an already chaotic few weeks. The entire vulnerabilities have an effect on Ivanti’s Join Safe and Coverage Safe VPN merchandise.
A tarnished fame and battered safety professionals
The brand new vulnerability got here to mild as two different vulnerabilities had been already beneath mass exploitation, largely by a hacking group researchers have stated is backed by the Chinese language authorities. Ivanti supplied mitigation steering for the 2 vulnerabilities on January 11, and launched a correct patch final week. The Cybersecurity and Infrastructure Safety Company, in the meantime, mandated all federal companies beneath its authority disconnect Ivanti VPN merchandise from the Web till they’re rebuilt from scratch and operating the newest software program model.
By Sunday, assaults concentrating on CVE-2024-21893 had mushroomed, from hitting what Ivanti stated was a “small variety of clients” to a mass base of customers, analysis from safety group Shadowserver confirmed. The steep line within the right-most a part of the next graph tracks the vulnerability’s meteoric rise beginning on Friday. On the time this Ars publish went dwell, the exploitation quantity of the vulnerability exceeded that of CVE-2023-46805 and CVE-2024-21887, the earlier Ivanti vulnerabilities beneath energetic concentrating on.

Shadowserver
Methods that had been inoculated towards the 2 older vulnerabilities by following Ivanti’s mitigation course of remained large open to the latest vulnerability, a standing that doubtless made it engaging to hackers. There’s one thing else that makes CVE-2024-21893 engaging to risk actors: as a result of it resides in Ivanti’s implementation of the open-source Safety Assertion Markup Language—which handles authentication and authorization between events—individuals who exploit the bug can bypass regular authentication measures and acquire entry on to the executive controls of the underlying server.
Exploitation doubtless received a lift from proof-of-concept code launched by safety agency Rapid7 on Friday, however the exploit wasn’t the only real contributor. Shadowserver stated it started seeing working exploits a number of hours earlier than the Rapid7 launch. The entire totally different exploits work roughly the identical means. Authentication in Ivanti VPNs happens by the doAuthCheck operate in an HTTP net server binary situated at /root/residence/bin/net. The endpoint /dana-ws/saml20.ws doesn’t require authentication. As this Ars publish was going dwell, Shadowserver counted a little bit greater than 22,000 situations of Join Safe and Coverage Safe.

Shadowserver
VPNs are an excellent goal for hackers in search of entry deep inside a community. The gadgets, which permit staff to log into work portals utilizing an encrypted connection, sit on the very fringe of the community, the place they reply to requests from any machine that is aware of the proper port configuration. As soon as attackers set up a beachhead on a VPN, they’ll typically pivot to extra delicate components of a community.
The three-week spree of continuous exploitation has tarnished Ivanti’s fame for safety and battered safety professionals as they’ve scrambled—typically in useless—to stanch the circulation of compromises. Compounding the issue was a sluggish patch time that missed Ivanti’s personal January 24 deadline by every week. Making issues worse nonetheless: hackers discovered tips on how to bypass the mitigation recommendation Ivanti supplied for the primary pair of vulnerabilities.
Given the false begins and excessive stakes, CISA’s Friday mandate of rebuilding all servers from scratch as soon as they’ve put in the newest patch is prudent. The requirement doesn’t apply to non-government companies, however given the chaos and problem securing the Ivanti VPNs in latest weeks, it’s a commonsense transfer that every one customers ought to have taken by now.






