Phishing assaults making the most of what seems to be a bug in Apple’s password reset function have change into more and more widespread, in keeping with a report from KrebsOnSecurity. A number of Apple customers customers have been focused in an assault that bombards them with an limitless stream of notifications or multi-factor authentication (MFA) messages in an try and get them to approve an Apple ID password change.
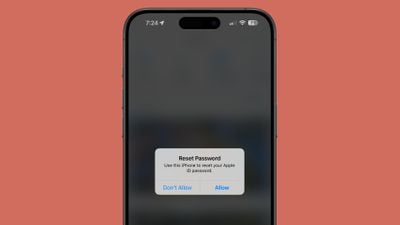
An attacker is ready to trigger the goal’s iPhone, Apple Watch, or Mac to show system-level password change approval texts over and over, with the hope that the individual being focused will mistakenly approve the request or get bored with the notifications and click on on the settle for button. If the request is accredited, the attacker is ready to change the Apple ID password and lock the Apple person out of their account.
As a result of the password requests goal the Apple ID, they pop up on all of a person’s units. The notifications render all linked Apple merchandise unable for use till the popups are dismissed one after the other on every gadget. Twitter person Parth Patel lately shared his expertise being focused with the assault, and he says he couldn’t use his units till he clicked on “Do not Permit” for greater than 100 notifications.
When attackers are unable to get the individual to click on “Permit” on the password change notification, targets typically get telephone calls that appear to be coming from Apple. On these calls, the attacker claims to know that the sufferer is below assault, and makes an attempt to get the one-time password that’s despatched to a person’s telephone quantity when making an attempt a password change.
In Patel’s case, the attacker was utilizing data leaked from a individuals search web site, which included title, present handle, previous handle, and telephone quantity, giving the individual making an attempt to entry his account ample data to work from. The attacker occurred to have his title unsuitable, and he additionally grew to become suspicious as a result of he was requested for a one-time code that Apple explicitly sends with a message confirming that Apple doesn’t ask for these codes.
The assault appears to hinge on the perpetrator accessing the e-mail handle and telephone quantity related to an Apple ID.
KrebsOnSecurity appeared into the problem, and located that attackers seem like utilizing Apple’s web page for a forgotten Apple ID password. This web page requires a person’s Apple ID e-mail or telephone quantity, and it has a CAPTCHA. When an e-mail handle is put in, the web page shows the final two digits of the telephone quantity related to the Apple account, and submitting within the lacking digits and hitting submit sends a system alert.
It’s not clear how the attackers are abusing the system to ship a number of messages to Apple customers, nevertheless it seems to be a bug that’s being exploited. It’s unlikely that Apple’s system is supposed to have the ability to be used to ship greater than 100 requests, so presumably the speed restrict is being bypassed.
Apple gadget homeowners focused by this sort of assault ought to make sure to faucet “Do not Permit” on all requests, and must be conscious that Apple doesn’t make telephone calls requesting one-time password reset codes.






