Microsoft
Microsoft is having one other whack at its controversial Recall function for Copilot+ Home windows PCs, after the unique model crashed and burned amid scrutiny from safety researchers and testers over the summer season. The previous model of Recall recorded screenshots and OCR textual content of all person exercise, and saved it unencrypted on disk the place it may simply be accessed by one other person on the PC or an attacker with distant entry.
The function was introduced in late Could, with out having gone by any of the general public Home windows Insider testing that almost all new Home windows options get, and was scheduled to ship on new PCs by June 18; by June 13, the corporate had delayed it indefinitely to rearchitect it and stated that it might be examined by the traditional channels earlier than it was rolled out to the general public.
At present, Microsoft shared extra in depth particulars on precisely how the safety of Recall has been re-architected in a publish by Microsoft VP of Enterprise and OS Safety David Weston.
Safer, additionally optionally available
Microsoft
The broad strokes of at this time’s announcement are much like the modifications Microsoft initially introduced for Recall over the summer season: that the function could be opt-in and off-by-default as an alternative of opt-out, that customers would wish to re-authenticate with Home windows Hi there earlier than accessing any Recall information, and that domestically saved Recall information might be protected with extra encryption.
Nonetheless, some particulars present how Microsoft is trying to placate skeptical customers. As an illustration, Recall can now be eliminated completely from a system utilizing the “optionally available options” settings in Home windows (when an analogous removing mechanism confirmed up in a Home windows preview earlier this month, Microsoft claimed it was a “bug,” however apparently not).
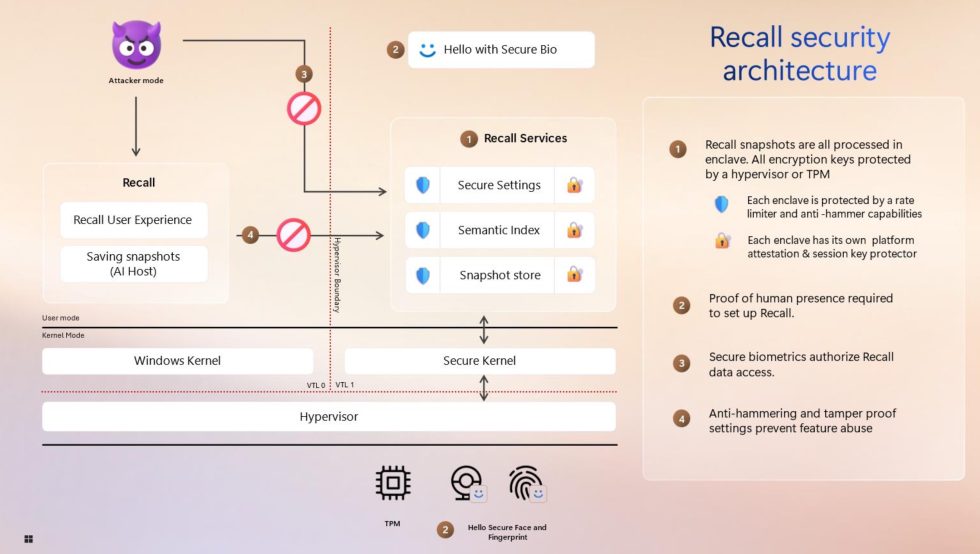
The corporate can be sharing extra about how Home windows will defend information domestically. All Recall information saved domestically, together with “snapshots and any related info within the vector database,” might be encrypted at relaxation with keys saved in your system’s TPM; based on the weblog publish, Recall will solely perform when BitLocker or Machine Encryption is totally enabled. Recall can even require Virtualization-Based mostly Safety (VBS) and Hypervisor-Protected Code Integrity (HVCI) enabled; these are options that individuals typically flip off to enhance recreation efficiency, however Recall will reportedly refuse to work except they’re turned on.
It is because the brand new Recall operates inside a VBS enclave, which helps to isolate and safe information in reminiscence from the remainder of the system.
“This space acts like a locked field that may solely be accessed after permission is granted by the person by Home windows Hi there,” writes Weston. “VBS enclaves supply an isolation boundary from each kernel and administrative customers.”
Home windows does not enable any code to run inside these enclaves that hasn’t been signed by Microsoft, which ought to decrease the danger of exposing Recall information to malware or different rogue purposes. Different malware protections new to this model of Recall embody “rate-limiting and anti-hammering measures.”

Microsoft
Microsoft is having one other whack at its controversial Recall function for Copilot+ Home windows PCs, after the unique model crashed and burned amid scrutiny from safety researchers and testers over the summer season. The previous model of Recall recorded screenshots and OCR textual content of all person exercise, and saved it unencrypted on disk the place it may simply be accessed by one other person on the PC or an attacker with distant entry.
The function was introduced in late Could, with out having gone by any of the general public Home windows Insider testing that almost all new Home windows options get, and was scheduled to ship on new PCs by June 18; by June 13, the corporate had delayed it indefinitely to rearchitect it and stated that it might be examined by the traditional channels earlier than it was rolled out to the general public.
At present, Microsoft shared extra in depth particulars on precisely how the safety of Recall has been re-architected in a publish by Microsoft VP of Enterprise and OS Safety David Weston.
Safer, additionally optionally available

Microsoft
The broad strokes of at this time’s announcement are much like the modifications Microsoft initially introduced for Recall over the summer season: that the function could be opt-in and off-by-default as an alternative of opt-out, that customers would wish to re-authenticate with Home windows Hi there earlier than accessing any Recall information, and that domestically saved Recall information might be protected with extra encryption.
Nonetheless, some particulars present how Microsoft is trying to placate skeptical customers. As an illustration, Recall can now be eliminated completely from a system utilizing the “optionally available options” settings in Home windows (when an analogous removing mechanism confirmed up in a Home windows preview earlier this month, Microsoft claimed it was a “bug,” however apparently not).
The corporate can be sharing extra about how Home windows will defend information domestically. All Recall information saved domestically, together with “snapshots and any related info within the vector database,” might be encrypted at relaxation with keys saved in your system’s TPM; based on the weblog publish, Recall will solely perform when BitLocker or Machine Encryption is totally enabled. Recall can even require Virtualization-Based mostly Safety (VBS) and Hypervisor-Protected Code Integrity (HVCI) enabled; these are options that individuals typically flip off to enhance recreation efficiency, however Recall will reportedly refuse to work except they’re turned on.
It is because the brand new Recall operates inside a VBS enclave, which helps to isolate and safe information in reminiscence from the remainder of the system.
“This space acts like a locked field that may solely be accessed after permission is granted by the person by Home windows Hi there,” writes Weston. “VBS enclaves supply an isolation boundary from each kernel and administrative customers.”
Home windows does not enable any code to run inside these enclaves that hasn’t been signed by Microsoft, which ought to decrease the danger of exposing Recall information to malware or different rogue purposes. Different malware protections new to this model of Recall embody “rate-limiting and anti-hammering measures.”




