This flaw affected customers of those gadgets: iPhone XS and later, iPad Professional 12.9-inch 2nd technology and later, iPad Professional 10.5-inch, iPad Professional 11-inch 1st technology and later, iPad Air third technology and later, iPad sixth technology and later, and iPad mini fifth technology and later. Somebody with one of many aforementioned gadgets tapping on a malicious picture may have given an attacker the chance to run any instructions or codes on the goal machine. The replace, as soon as put in, removes this vulnerability from the affected gadgets.
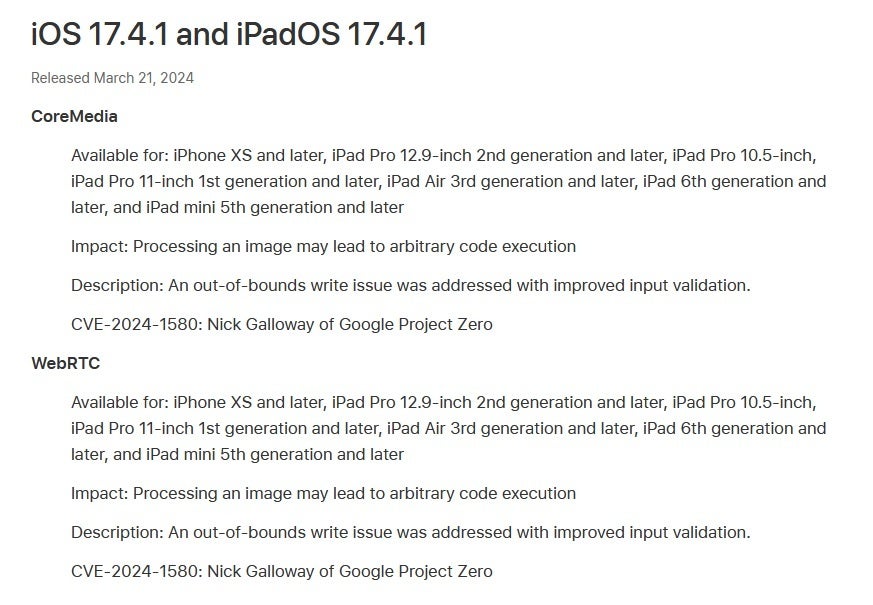

Apple updates its Safety Releases assist web page to disclose the issues mounted by iOS 17.4.1 and iPadOS 17.4.1
Apple did not say that it had any indication that the vulnerability was exploited. The easy description given by Apple learn like this: “An out-of-bounds write difficulty was addressed with improved enter validation.” Given the CVE-2024-1580 itemizing quantity, the flaw was found by Google Mission Zero’s Nick Galloway.
The second vulnerability was a flaw within the system Apple calls WebRTC which offers “internet browsers and cell functions with real-time communication through utility programming interfaces.” This flaw additionally impacted the identical gadgets which we are going to gladly repeat: iPhone XS and later, iPad Professional 12.9-inch 2nd technology and later, iPad Professional 10.5-inch, iPad Professional 11-inch 1st technology and later, iPad Air third technology and later, iPad sixth technology and later, and iPad mini fifth technology and later.
This vulnerability, additionally not exploited by any attackers so far as Apple may inform, additionally would have allowed an attacker to run any instructions or codes on a focused machine. The flaw was assigned CVE quantity CVE-2024-1580 and was additionally found by Nick Galloway of Google Mission Zero
If you have not put in iOS 17.4.1 but, go to Settings > Normal > Software program Replace and observe the instructions.
This flaw affected customers of those gadgets: iPhone XS and later, iPad Professional 12.9-inch 2nd technology and later, iPad Professional 10.5-inch, iPad Professional 11-inch 1st technology and later, iPad Air third technology and later, iPad sixth technology and later, and iPad mini fifth technology and later. Somebody with one of many aforementioned gadgets tapping on a malicious picture may have given an attacker the chance to run any instructions or codes on the goal machine. The replace, as soon as put in, removes this vulnerability from the affected gadgets.


Apple updates its Safety Releases assist web page to disclose the issues mounted by iOS 17.4.1 and iPadOS 17.4.1
Apple did not say that it had any indication that the vulnerability was exploited. The easy description given by Apple learn like this: “An out-of-bounds write difficulty was addressed with improved enter validation.” Given the CVE-2024-1580 itemizing quantity, the flaw was found by Google Mission Zero’s Nick Galloway.
The second vulnerability was a flaw within the system Apple calls WebRTC which offers “internet browsers and cell functions with real-time communication through utility programming interfaces.” This flaw additionally impacted the identical gadgets which we are going to gladly repeat: iPhone XS and later, iPad Professional 12.9-inch 2nd technology and later, iPad Professional 10.5-inch, iPad Professional 11-inch 1st technology and later, iPad Air third technology and later, iPad sixth technology and later, and iPad mini fifth technology and later.
This vulnerability, additionally not exploited by any attackers so far as Apple may inform, additionally would have allowed an attacker to run any instructions or codes on a focused machine. The flaw was assigned CVE quantity CVE-2024-1580 and was additionally found by Nick Galloway of Google Mission Zero
If you have not put in iOS 17.4.1 but, go to Settings > Normal > Software program Replace and observe the instructions.






