In context: Because the first pc virus, malware has been a cat-and-mouse sport between hackers and safety researchers. It is to the purpose the place most malware is thought, at the least in sort and supply technique. Nevertheless, unhealthy actors sometimes conceive a brand new trick to cover their footprints and idiot the white hats.
Safety analytics agency Mandiant lately uncovered a “never-before-seen” assault chain that used Base 64 encoding on at the least two totally different web sites to ship the second-stage payload of a three-stage malware. The 2 websites had been tech publication Ars Technica and video internet hosting web site Vimeo.
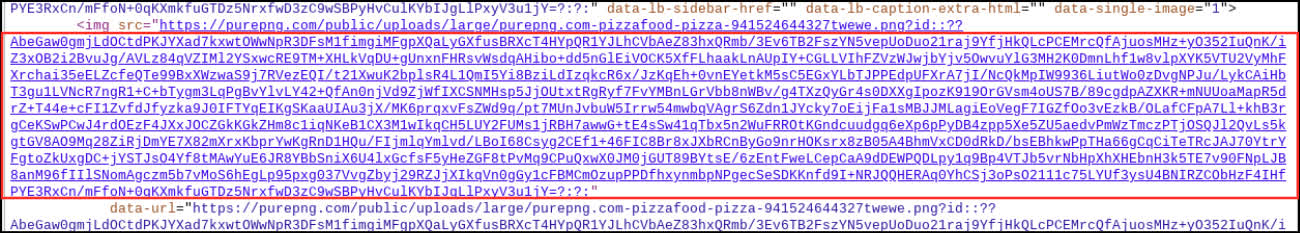
A consumer posted an image of a pizza on the Ars Technica discussion board with the caption, “I like pizza.” There was nothing inherently mistaken with the picture or textual content. Nevertheless, the picture, hosted on a third-party web site, had a URL containing with a Base 64 string. Base 64 transformed to ASCII seems to be like random characters, however on this case, it obfuscated binary directions to obtain and set up the second stage of a malware package deal. In one other occasion, an an identical string appeared within the description of an in any other case innocent video on Vimeo.
An Ars Technica spokesperson mentioned it eliminated the account – created final November – after an nameless consumer tipped off the web site concerning the unusual hyperlink for the picture (under).
Mandiant mentioned it recognized the code as belonging to a risk actor named UNC4990, which it has tracked since 2020. For many customers, the directions had no impact. It solely operates on gadgets that already comprise the primary stage of the malware (explorer.ps1). UNC4990 distributed stage one by means of contaminated flash drives configured to hyperlink to the file hosted on GitHub and GitLab.
The second stage, dubbed “Emptyspace,” is a textual content file that seems clean to browsers and textual content editors. Nevertheless, opening it with a hex editor reveals a binary file that makes use of a intelligent encoding scheme of areas, tabs, and new strains to create executable binary code. Mandiant admits it has by no means seen this system used earlier than.
“It is a totally different and novel approach we’re seeing abuse that may be fairly arduous to detect,” Mandiant researcher Yash Gupta mentioned instructed Ars. “That is one thing in malware we’ve got not sometimes seen. It is fairly attention-grabbing for us and one thing we wished to name out.”
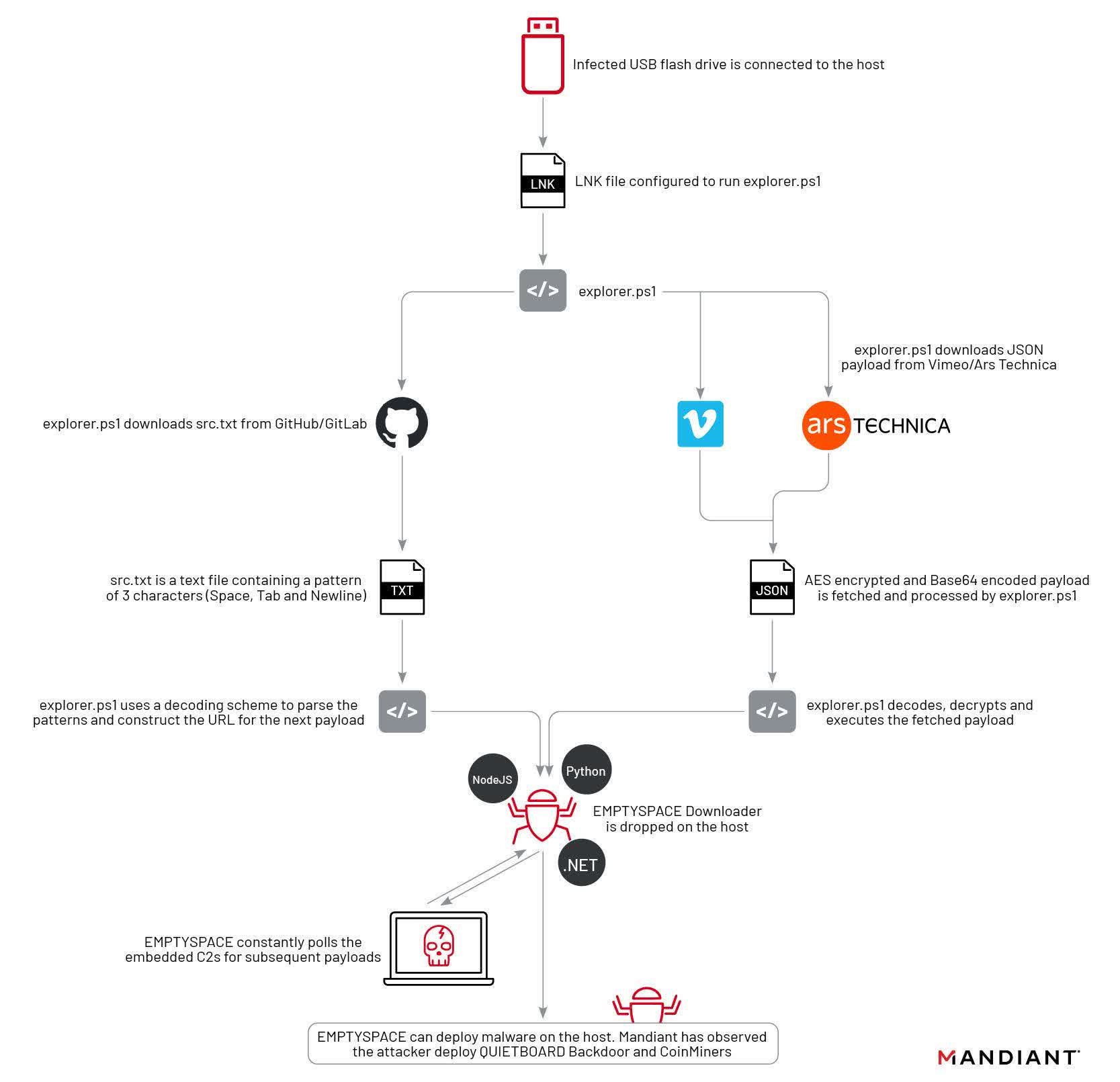
Upon execution, Emptyspace repeatedly polls a command and management server and downloads a backdoor dubbed “Quietboard” on command. UNC4990 makes use of the backdoor to put in cryptocurrency miners on the contaminated machines. Nevertheless, Mandiant says it has solely tracked a single occasion of a Quietboard set up.
Given the rarity of Quietboard, UNC4990’s assault poses a minimal risk. Nevertheless, explorer.ps1 and Emptyspace situations could possibly be a lot larger, leaving customers susceptible. Mandiant explains tips on how to detect the an infection in its weblog.